Quarterly Security Update: July 2025
Here’s a snapshot of the latest malware trends affecting businesses everywhere, new and notable threats plus the latest top tips from our IT security team.
Malware Trends
- Total network-based malware detections increased again, rising 171% since last quarter.
- Overall Endpoint total malware volume was down. However, we also saw a huge (712%) rise in new unique malware variants on the endpoints. This signals a sharp rise in evasive and sophisticated malware (trojans, information stealers, coinminers and phishing threats).
- Attackers continue to use encryption to spread malware, with 71% of malware arriving over encrypted (TLS) connections – a continued increase for the year.
- AI tools are developing sophisticated threats quickly at scale.
- Ransomware declined 85% from last quarter. Attackers are now shifting toward data theft instead of encryption (as improvements in data backups and recovery have been made).
- For years, malicious scripts have remained the most common way malware arrives on an endpoint. However, this quarter we saw browsers and “other” vectors rise significantly, suggesting that attackers are returning to “drive-by download” tactics and delivering malware more often in piracy-related tools and remote software.
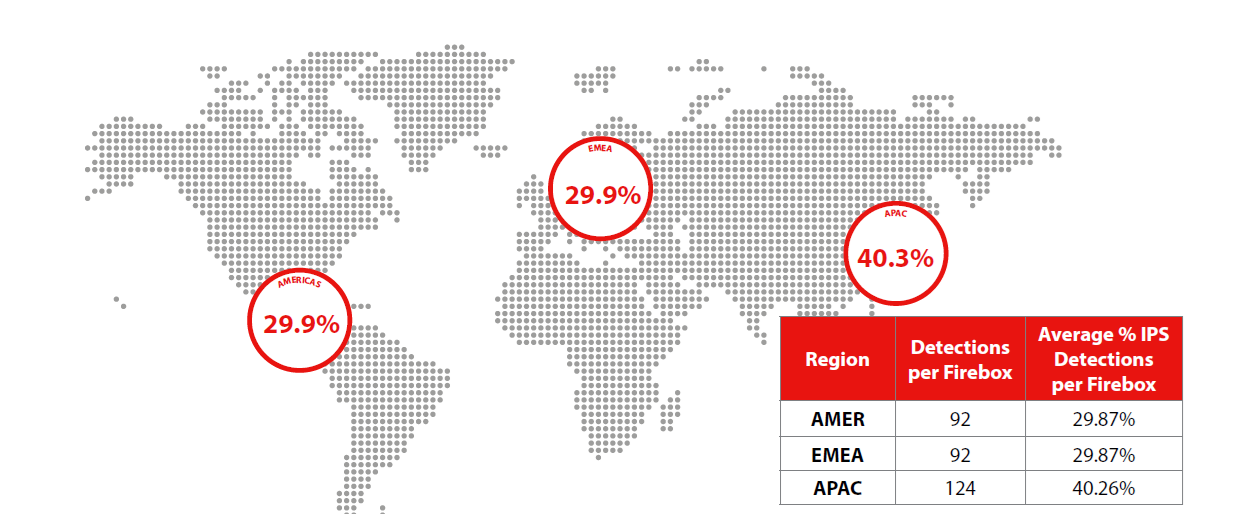
Malware threats by region
Top 10 Malware Detections
 Spotlight: Windows 10 ends this October
Spotlight: Windows 10 ends this October
The deadline to upgrade to Windows 11 is now a mere couple of months away so it’s time to start planning for any work devices still on Windows 10. If you or any of your workforce sit back and do nothing, this could / will be a major impact on your IT Security. Read our guide to upgrading and your options.
Your Key takeaways for this Quarter
AI – Fight fire with fire
This quarter, we have seen AI tools really infiltrating the hacker underground. Most phishing tactics have incorporated various levels of AI to assist in writing convincing emails and even automating the generation of more targeted spear phishing. Attackers are also leveraging AI to write new malware or adjust it to evade detection. This is set to grow.
The only solution is to also leverage powerful AI technologies for defence. Here at GHM, our solutions feature more AI technologies in all our network, endpoint, and identity products.
Increase or update your web protections
As mentioned above, we have seen web browsers jump onto the scene as a top infection vector, suggesting that attackers are bringing back drive-by download attacks.
You likely have some web-based defences already, but it might be time to re-check them and add new ones. Talk to us about the options to protect your web servers and clients.
Toughen up remote access
Step 1: never expose remote access without multi-factor authentication (MFA). This step alone can protect you from a huge majority of remote access attacks. Follow the normal best password and credential practices and use unique and strong passwords or other strong credentials.
Step 2: require VPN or zero trust network access (ZTNA) authentication before allowing users to access remote access tools.
Step 3: Finally, as always, patch your remote access, VPN, and ZTNA tools aggressively, and check all of your remote access apps to see if they have any app-specific hardening options/settings.
If you’re concerned or would like to chat about anything covered in this article, reach out to our IT Support team on 01865 367111 who will be happy to help.