Welcome to our first Security Update! Each quarter, our IT Support experts will bring you a snapshot of the latest malware trends, new and notable threats plus the latest top tips from our security experts. Let’s get cracking!
Malware trends
*Thanks to our partners at Watchguard for the following insight from their recently published industry leading Threat Lab Report (Q4 2024)
- Total network-based malware detections almost doubled, increasing 94%. Network exploits continued to bombard organisations in Q4 2024, with attack volumes remaining high and a mix of both old and new threats. In fact, many tried-and-true exploits persisted as top attacks this quarter, underscoring that attackers stick with what works.
- Strangely, endpoint unique malware detection shows a completely different picture, decreasing about 91% QoQ, and showing the lowest volume of unique detections we saw last year.
- Not only were endpoint unique malware detections down, but new malware threats also hit an all-time low of only 8 new threats per 100,000 malware detections. In general, we saw less targeted malware that only affected one or a few machines, and rather generic, sometimes-old malware that affected many machines
- 60% of malware spread over encrypted connections (TLS) during Q4, which is an 8pt increase from last quarter, and a continued increase for the year, indicating the growing role in more proactive anti-malware services catching sophisticated, evasive malware, like zero-day malware, when it comes from encrypted channels
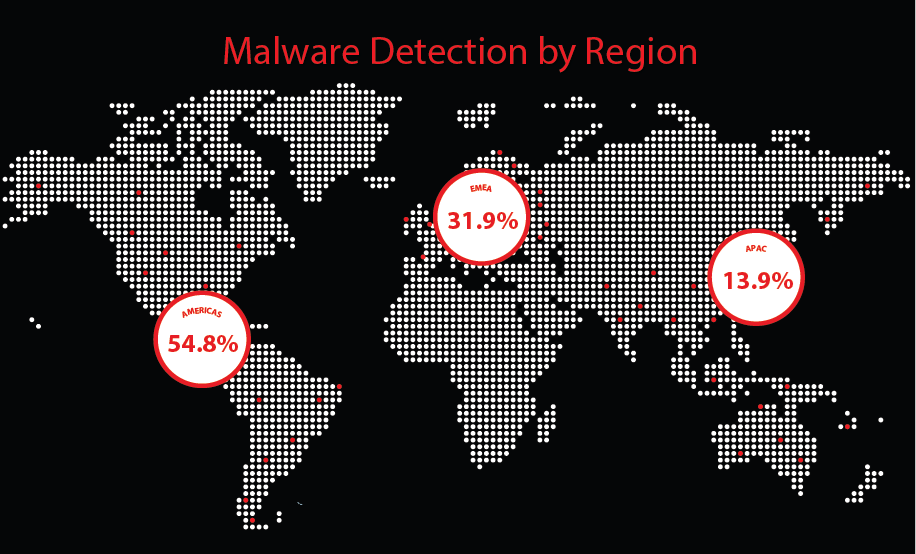
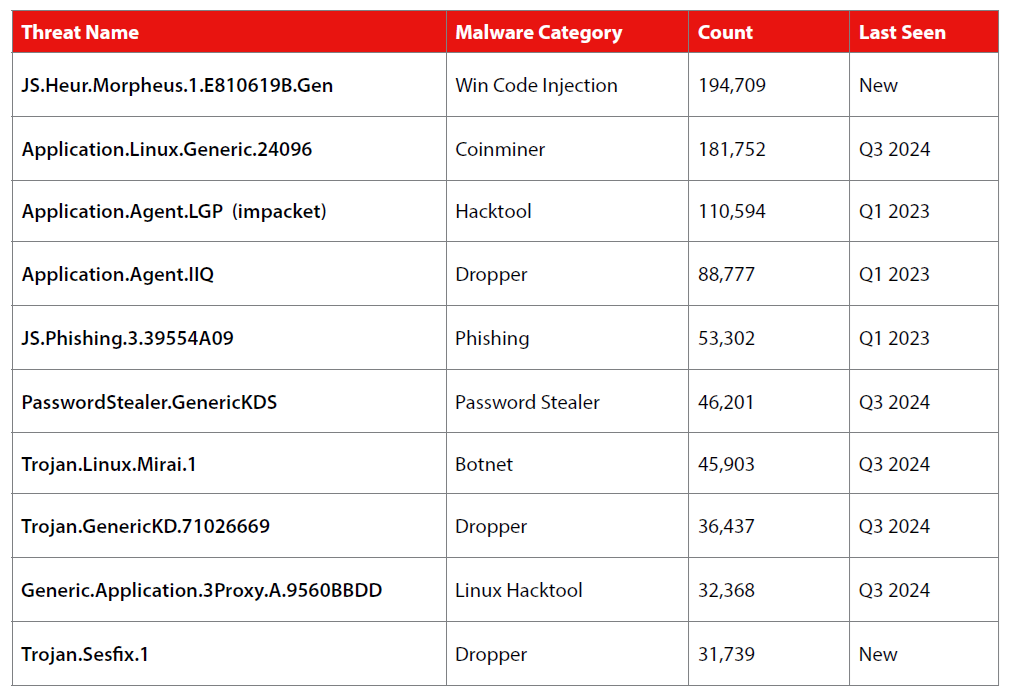
New & notable threats
JS.Heur.Morpheus.1.E810619B.Gen – a Windows code injection malware with 194,709 detections. It often arrives via an email with a zipped attachment, which, when opened, connects to 0x0[.]st through a VBA script. Embedded within is a PowerShell script that installs a keylogger and spyware, quietly compromising systems.
Trojan.Sesfix.1 – A new malware detection identifies a VBA script. A Microsoft Office File will usually run this type of script; however, in this case another VBA script The malware installs xmrig, a coinminer.
Application.Agent.LGP (Impacket) – It’s built to manipulate low-level network protocols with precision. It can target Windows systems SMB shares or execute commands remotely on a machine.
JS.Phishing.3 – This phishing tactic exploits trust in familiar interfaces, making it dangerously effective. Once credentials are harvested, attackers can infiltrate email, Cloud storage, or corporate systems, often undetected until it’s too late. To stay safe, always verify the URL before logging in.
Spotlight: Social Engineering – beware the fake IT help desk
The National Cyber Security Centre (NCSC) has warned that criminals launching cyber attacks at British retailers are impersonating IT help desks to break into organisations. This is how hackers targeted Marks & Spencer, Co-op and Harrods in recent weeks. GHM will always authenticate who we are when calling our support desk.
Other examples of social engineering techniques that employees should watch out for right now include offers of free software, work-related emails that look real or official, surfing social media during work, accepting fake LinkedIn invitations and name-dropping in emails.
Spotlight: Coin miners
The Threat Lab also observed a significant increase in crypto miner detection at 141% quarter over quarter. Cryptocurrency mining is a natural process for acquiring cryptocurrency on some blockchains, including Bitcoin. A malicious coin miner can look like executing software that installs a coin miner without the user’s knowledge or consent. Like any phishing, treat employees as the first line of defence against these types of cyberattacks.
KEY TAKEAWAYS
Patch, patch, patch. Companies should focus on a two pronged approach of patching old holes and keeping up with new threats. Strive to patch everything possible as quickly as you can. If that’s unachievable, take the time to develop a risk-based policy. Employ automated patching (check with your MSP that automated patching can be done with the Remote Monitoring and Management (RMM) solution they use as not all do it).
Here at GHM we combine automated patching with good old fashioned manual checks and recently moved a new client from a threat score of 80% down to 0% using this approach.
Protect Linux computers, Macs and IoT the same as Windows. We all now that attackers, by far more often, target the Windows operating system (OS) with malware and attack it over any other. However, just because Windows is the biggest target doesn’t mean attackers aren’t targeting other devices. This quarter, we saw a rise in Top 20 malware that affected Linux machines, including coinminers, which tend to prefer Linux servers. In short, your server should have good endpoint detection and response software too. Luckily our products like EPDR work great on Windows, Mac, or Linux machines.
Embrace a Defence-in-Depth Approach to Combat Evolving Malware. We have observed fluctuations in the prevalence of network and endpoint malware; while this quarter’s findings indicate a rise in network-based threats, endpoint malware detections have notably decreased. This dynamic nature of threats requires a multi-layered approach to ensure comprehensive protection against the diverse tactics employed by cybercriminals
