Each quarter, we’ll bring you a snapshot of the latest malware trends, new and notable threats plus the latest top tips from our security experts. Thanks to our partners at Watchguard for the following insight from their recently published industry leading Threat Lab Report (Q2 2025)
Notable trends
Over the last few quarters, malware – especially network-detected malware – has grown in volume, increasing an additional 15% during Q2 2025. More importantly, we have seen the amount of malware evading signature-based detection (zero-day malware) and using encryption increase to highs seen only in previous record quarters. This suggests that attackers are focusing on more evasive malware, and we too must focus on more advanced protection technologies, like those of endpoint detection and response products (talk to our specialists for our solutions).
Network-based attacks and software exploits also grew a little (8.3%), thought unique types of network attacks fell. We saw new generic SQL injection signature detect a far bigger number of this class of attacks, along with a lot of web application attacks in general.
Total malware was down slightly but new unique malware variants increased again, as mentioned above. The way threat actors deliver malware also continues to evolve away from scripts, and more towards browser-based attacks, which suggest we should watch out for an increase in drive-by download attacks.
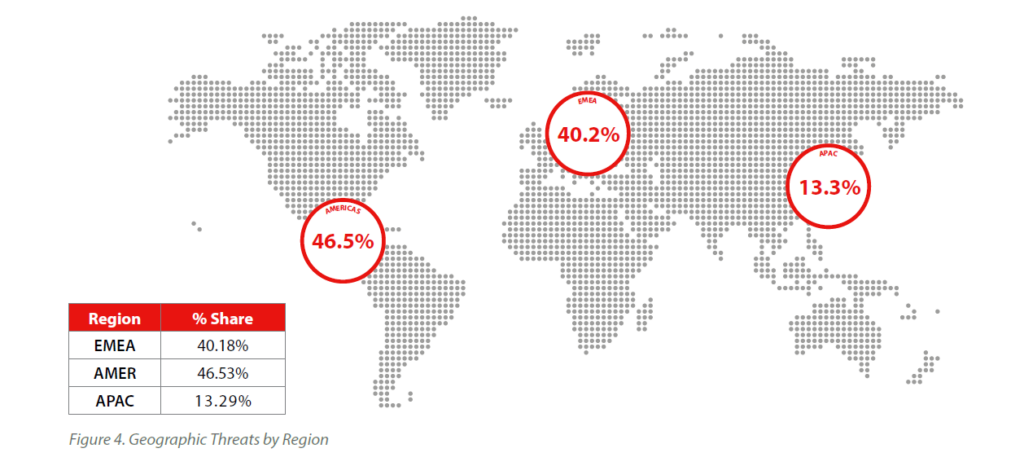
Malware threats by region
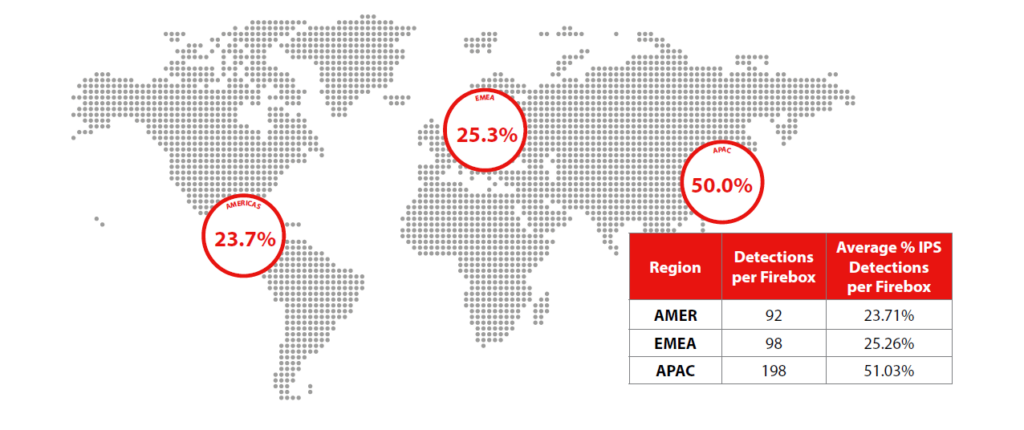
 Network threats by region
Network threats by region
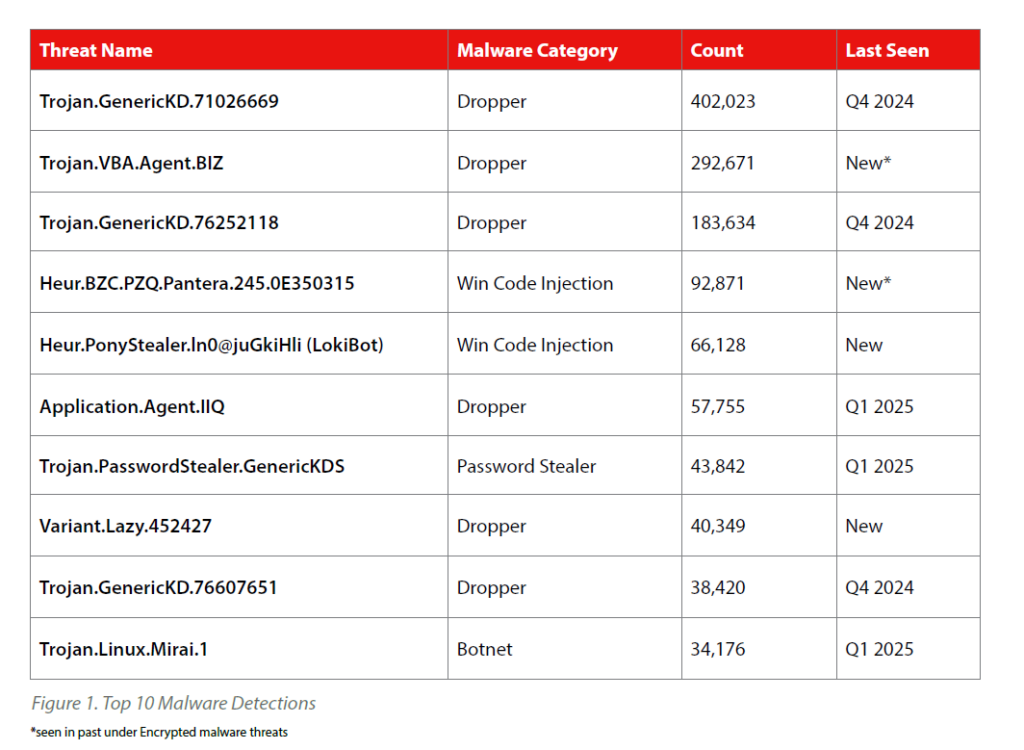
 Top 10 Malware Detections
Top 10 Malware Detections
Among the standout threats, Trojan.VBA.Agent.BIZ, a dropper with 292,671 detections, emerges as a new variant of Trojan.Agent.VBS. This evolution incorporates VBA macros in Office documents to deliver payloads, exploiting user-enabled macros for initial compromise. First seen this last quarter, it underscores rapid adaptation, making it a prime target for enhanced email and document scanning.
Another notable entry, Heur.PonyStealer.ln0 @ juGkiHli, a Win code injection threat with 66,128 detections, is a fresh malware strain often used to deploy botnets like LokiBot. This variant injects code into legitimate processes, enabling credential theft, keystroke logging, and C2 communication.
New Network Detections
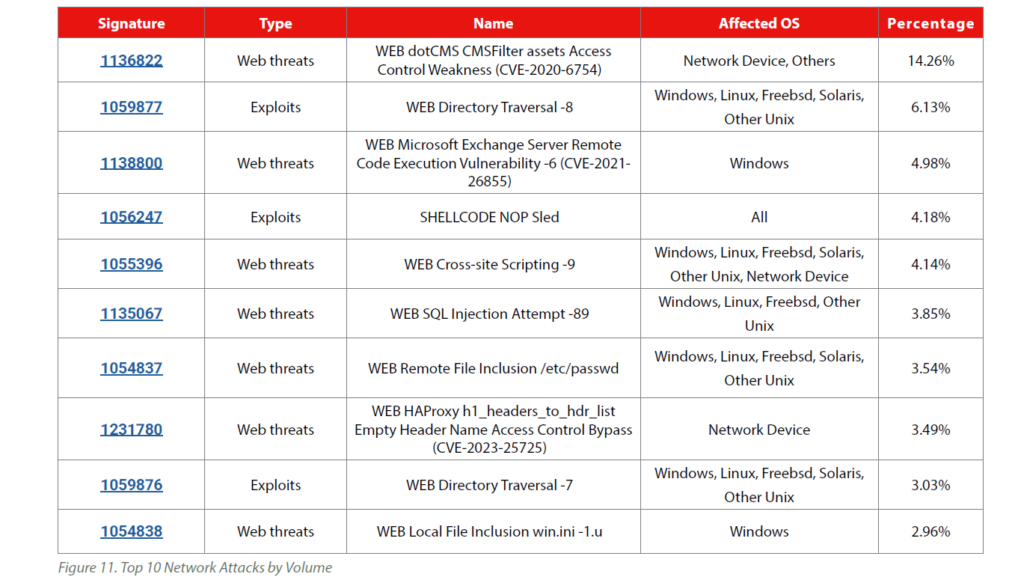
Notably, an exploit targeting dotCMS , “WEB dotCMS CMSFilter assets Access Control Weakness (CVE-2020-6754)”, took the #1 spot this quarter after first making an appearance in the Q2 2024 report. This vulnerability (first seen in 2020) allows unauthorized access to web assets and was previously ranked #2 in Q1. Its rise to #1 suggests an uptick in exploit attempts against unpatched content management systems.
Last quarter’s top attack, a generic directory traversal attempt (ID 1059877), fell to #2 in comparison. This longstanding file path traversal signature (which detects attempts to access unauthorised files via crafted URLs) remains a constant threat to web servers, even as its volume decreased from Q1.
New: Top Phishing Domains
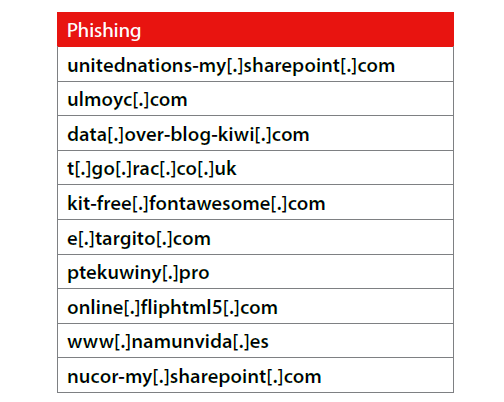
As a reminder, phishing domains are directly associated with social engineering campaigns.Their most common objectives include tricking victims into willingly entering credentials into legitimate-looking authentication portals, or convincing them to run malware on their machines.
Spotlight: The Ransomware Landscape
Detections and extortions both decreased this quarter – although you might not think it seeing all of the high profile breaches. However, more ransomware groups are popping up indicating that the problem is getting slightly worse as more people turn to cybercrime. There were 18 new ransomware groups in Q2, and only 10 of the previous groups went dormant or no longer exist. One of those groups is LockBit, which keeps reinventing itself and is still around. WikiLeaksV2 is believed to be related to the Qilin group. So, realistically, it’s only about the right groups seizing operations.
Your key takeaways!
Consider a USB security strategy
Here is an overview of what you should be doing to protect USB devices and your users from this sort of threat:
• Have a policy telling users the acceptable use guidelines of personal and corporate USB storage devices. In general, most companies need to allow some for data transfer, but you should try to limit employees using personal ones as much as possible.
• Disable autoplay or any USB autoload mechanism: In Windows, be sure to disable things like AutoPlay and AutoRun. Meanwhile, OSs (like macOS) may also allow you to force users to decide whether to allow USB devices every time they are plugged in. While this still puts the control in the user’s hands, the
mechanism still allows users to consider the risk when plugging in new devices.
• Always scan malware on USB devices. Be sure they are always configured to automatically scan any USB device a user plugs into your system.
Toughen up your web browsers
With the rise in browser-based malware the last few quarters, we believe drive-by download attacks may be on the upswing and suggest you spend some time hardening your browsers to these types of attacks. Here are some browser hardening tips:
• Patch and Update quickly
• Beware and train on browser social engineering
• Disable the browser password store and use an enterprise password manager
• Use plugins to disable active scripts by default
• Leverage EDR software, or USB device management, to limit USB devices
You need advanced malware prevention, detection and response
During Q2, both malware arriving over encrypted connections and zero-day malware increased. Zero-day malware – not detected by signatures – represented over three-fourths or more of all malware. This shows attackers are working harder to evade legacy or basic anti-malware controls, especially signature-based protection.
Every business needs more advanced anti-malware prevention and detection to stop this advanced and evasive malware. In general, endpoint detection and response (EDR) solutions tend to include more proactive and advanced methods of detecting malware, including but not limited to behavioural analysis of files and machine learning or AI-based detection. We highly recommend you use both network and endpoint solutions that offer these sorts of advanced and proactive malware detection mechanisms. Talk to our experts about our advanced malware solutions.